Answers

May 12, 2019 - 12:36 AM
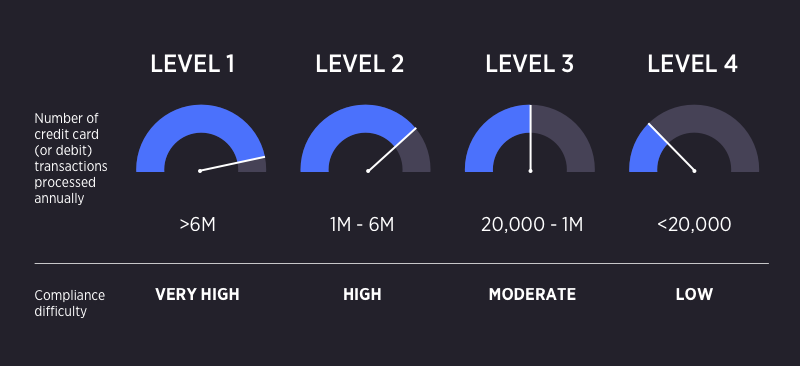
PCI compliance difficulty levels. Image source: BigCommerce
Over the last few years, we have witnessed a tremendous increase in E-commerce transactions to the delight of e-commerce business owners. It shows that more and more consumers are trusting the security provided by online stores throughout the process of internet shopping.
In response to the increase in trust by consumers, e-commerce store owners and online entrepreneurs are forced to provide safeguards that will protect consumer data continually.
As part of the mission of the PCI Security Standards Council (SSC), they state clearly that "the security of cardholder data effects everybody."
This means that E-commerce business owners have to take the responsibility of creating an environment where loyal customers can trade, feeling safe and confident that the payment information they provide would be safe enough.
In turn, the interest of merchants is taken into consideration too in the design and implementation of a set of regulations that would protect their investment. As part of its duty, PCI provides such backup for e-commerce businesses.
What Is The PCI Security Standards Council?
The PCI Security Standards Council is "a worldwide forum for ongoing creation, development, adjustment, dissemination, implementation, and storage of security standards for the protection of account data."
Usually, it is your compliance with the regularly updated standards of PCI combined with best practices that keep your system secure and fit for online transactions.
By remaining diligent to adhering to best practices covered by updates, you will be showing your customers that you stay resolute to being a part of the solution that protects their data in the online shopping world.
Risks Faced By E-Commerce Businesses in Dealing With Account Information of Customers
Today, more than ever before, we see the sophistication of methods used by cyber-attackers who are willing and always able to hack into e-commerce businesses and any other business. One major case that is worth mentioning at this juncture is that of eBay Inc. when it suffered an intrusion in 2014 and requested all customers to change their passwords.
You can easily imagine the level of damage such data breach would have caused for the corporation. The long history of eBay, along with how quickly it detected and reported the data compromise to stakeholders made the company hold on right.
The experience of eBay is one that has gotten even more common these days, but the level of compliance to standard and best practices they adopted for protecting customer data was part of what spared them and all stakeholders involved from more significant damage.
So, What are the Accepted E-commerce Best Practices for PCI Compliance and Cyber Security?
According to Foregenix, the past four years have brought about an exponential increase in online shopping - along with EMV (Europay, MasterCard and Visa Pay) in the US.
In 2013, New rules, standards and regulations where set, but in January 2017, the Best Practices Guide set by PCI was revised and expanded to cover areas that had been neglected before.
Here, take a look at a few highlights from the revised best practices guide you should pay special attention to while implementing your own e-commerce business.
Choosing Public Key Certificate Authorities
To a large extent, your digital certification is charged with providing authentication between your web server and e-commerce business browser.
It is the certificate that brings an additional protection layer - jumbling the message for a short while, during its transit between the browser and the web server that was incorporated into the process of encryption.
Digital certification takes charge of offering authentication and encryption, and both are essential tools when it comes to protecting the private data of your customers as they go about making their online purchases
Understand Your Sensitive Data - Its Location and Who is Responsible for Protecting It
Whatever the size of your business, you still need to understand everything that happens to the sensitive data of your customers as soon as it enters into the business data processing, transmission, and storage system.
As confidential information from your customer comes into your business processes, you become charged with the responsibility of maintaining security and integrity of data.
Sensitive data ranges from personal identifiable information to financial information like credit card numbers. Make sure that you identify every angle within the business environment, processes, and systems that sensitive data passes through.
Avoid Storing Sensitive Data, But If You Have It, Secure It
One big step towards protecting your business from security risks is by not storing cardholders data at all. As sensitive data enter and reside in your business process, ask yourself if there is any real need for the information to be retained and stored.
The more items you can take out, the better for you. However, if there is a good reason why you should store sensitive data, then you should secure it using the following steps:
Limit access to the database to only the people that need it, issuing each party their unique credentials;
Do not involve yourself in storing authentication data for your employees or customers.
Adopt the implementation of a tokenized solution that enables customers to be able to securely store their payment information and access it whenever they need to.
Use Firewalls to Protect Perimeters
To ensure proper security, you must be able to incorporate multiple layers of protection. A significant requirement of the PCI DSS is that you have a well-configured firewall in place for cyber-defense. It is essential for you to configure your firewalls properly, taking how your business handles data into consideration.
Fortify Your Interior With the Right People, Technology and Procedures
One weak link in the security chain is humans - especially employees; you should, therefore, be ready to organize security awareness training from time to time, irrespective of your business size.
From a technological standpoint, merchants should learn to incorporate payment technologies that are approved for PCI DSS compliance. Every merchant is required by PCI SSC to as a matter of ongoing concern, regularly review and maintain a list of validated payment applications.
Securing sensitive information should be the business of everybody if the global progress that we've seen so far in the adoption of E-commerce would continue.
Business owners must understand that they stand as much risk as the consumers themselves and so work hard towards best practices that will help to secure the process.

May 13, 2019 - 12:19 PM
https://ics-cert-training.inl.gov/learn
Although you probably don’t think of the DHS as having much in common with ecommerce cybersecurity, they actually offer 11 great free cybersecurity courses, as well as other training materials to supplement what you learn. Since the courses cover lots of subjects, from cybersecurity basics to ever-changing vulnerability trends, you can pick and choose what works best for your team.
Square’s PCI Compliance Guidehttps://squareup.com/guides/pci-compliance
Whether or not you use Square as part of your business, you might benefit from their long and detailed online guide to PCI compliance. You can skim the basics at the top, or delve into any aspect in the “Deep Dive” section. While Square does make a bid for your business at the bottom of the page, most of the content is strictly informational.
Future Learn’s Introduction to Cyber Securityhttps://www.futurelearn.com/courses/introduction-to-cyber-security
This course gives an entry-level overview into cybersecurity over the course of eight weeks (with three hours of study time per week). It’s free, accredited by the Institute of Information Security Professionals, and is a UK Government Communications Headquarters certified training. Upon completion, users get a certificate of achievement.
NIST’s Computer Security Resource CenterThe National Institute of Standards and Technology (NIST) offers a collection of cybersecurity publications, news, and more that users can browse by topic. The site also has a useful glossary where you can quickly look up relevant terms. However, this extensive library of reading material might seem overwhelming to cybersecurity beginners, so it’s probably best to take an introductory course (like Future Learn’s option above) before diving in.
Springboard’s Foundations of Cybersecurity
https://www.springboard.com/resources/learning-paths/cybersecurity-foundations/
Springboard offers another free introductory course for those just getting started with cybersecurity concepts. With this course, you get access to 38 total hours of content. After thoroughly covering the fundamentals, you can easily decide which aspects to dive deeper into. This course is aimed mainly at people who intend to start working in cybersecurity, but lots of it will certainly be relevant to your staff, too.
Security Now! Podcast
https://www.grc.com/securitynow.htm
This popular podcast makes a great supplement to the other courses and readings here, offering up-to-date information and interesting perspectives on the cybersecurity world. New episodes come out weekly, so it’s an easy way to stay abreast of the latest cybersecurity news and changes.
Stanford’s Free Cybersecurity Webinars
https://computersecurity.stanford.edu/free-online-videos
Stanford University has a handful of cybersecurity webinars available for free, covering subjects like cybersecurity trends and lessons learned from major breaches. You can also follow the “Computer Security Today” series for expert perspectives on different cybersecurity topics.
Cybrary’s Crowdsourced Resources
https://www.cybrary.it/catalog/
Cybrary offers crowdsourced resources shared among more than two million users. Most of the content is free, including courses, videos, and more. You can also take practice tests and assessments to test out your knowledge. Although users will need to parse through a large amount of content to choose what they want, you can find relevant trainings for beginners, experts, and anyone in between here.





Add New Comment